2.6 KiB
| type | stage | group | info |
|---|---|---|---|
| tutorial | Govern | Threat Insights | To determine the technical writer assigned to the Stage/Group associated with this page, see https://about.gitlab.com/handbook/product/ux/technical-writing/#assignments |
CVE ID request (FREE SAAS)
Introduced in GitLab 13.4, only for public projects on GitLab.com.
A CVE identifier is assigned to a publicly-disclosed software vulnerability. GitLab is a CVE Numbering Authority (CNA). For any public project you can request a CVE identifier (ID).
Assigning a CVE ID to a vulnerability in your project helps your users stay secure and informed. For example, dependency scanning tools can detect when vulnerable versions of your project are used as a dependency.
A common vulnerability workflow is:
- Request a CVE for a vulnerability.
- Reference the assigned CVE identifier in release notes.
- Publish the vulnerability's details after the fix is released.
Prerequisites
To submit a CVE ID Request the following prerequisites must be met:
- The project is hosted on GitLab.com.
- The project is public.
- You are a maintainer of the project.
- The vulnerability's issue is confidential.
Submit a CVE ID request
To submit a CVE ID request:
-
Go to the vulnerability's issue and select Create CVE ID Request. The new issue page of the GitLab CVE project opens.
-
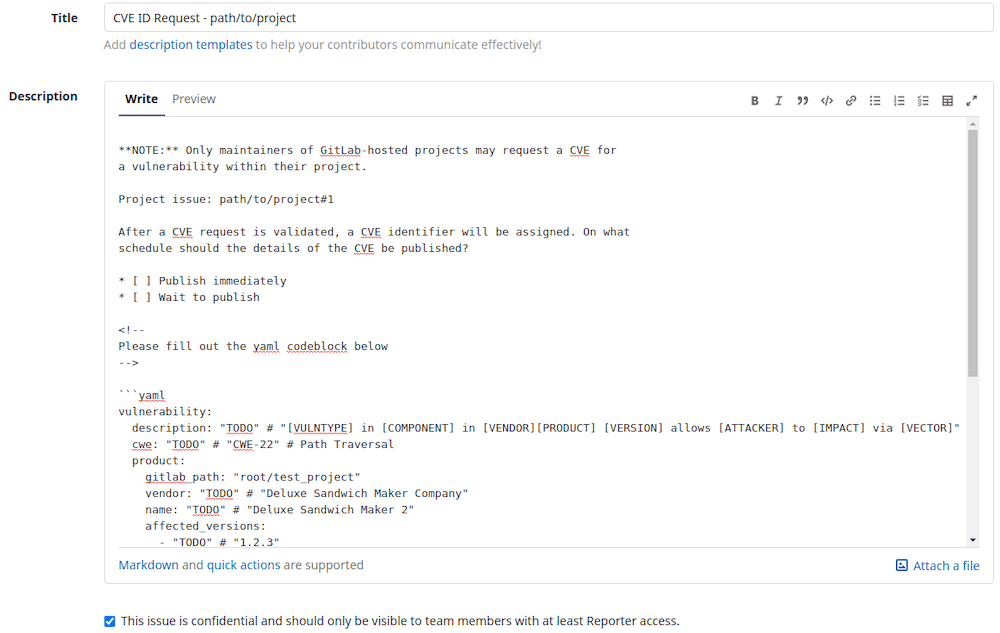
In the Title box, enter a brief description of the vulnerability.
-
In the Description box, enter the following details:
- A detailed description of the vulnerability
- The project's vendor and name
- Impacted versions
- Fixed versions
- The vulnerability class (a CWE identifier)
- A CVSS v3 vector
GitLab updates your CVE ID request issue when:
- Your submission is assigned a CVE.
- Your CVE is published.
- MITRE is notified that your CVE is published.
- MITRE has added your CVE in the NVD feed.
CVE assignment
After a CVE identifier is assigned, you can reference it as required. Details of the vulnerability submitted in the CVE ID request are published according to your schedule.