3.2 KiB
| stage | group | info | type |
|---|---|---|---|
| none | unassigned | To determine the technical writer assigned to the Stage/Group associated with this page, see https://about.gitlab.com/handbook/engineering/ux/technical-writing/#assignments | reference |
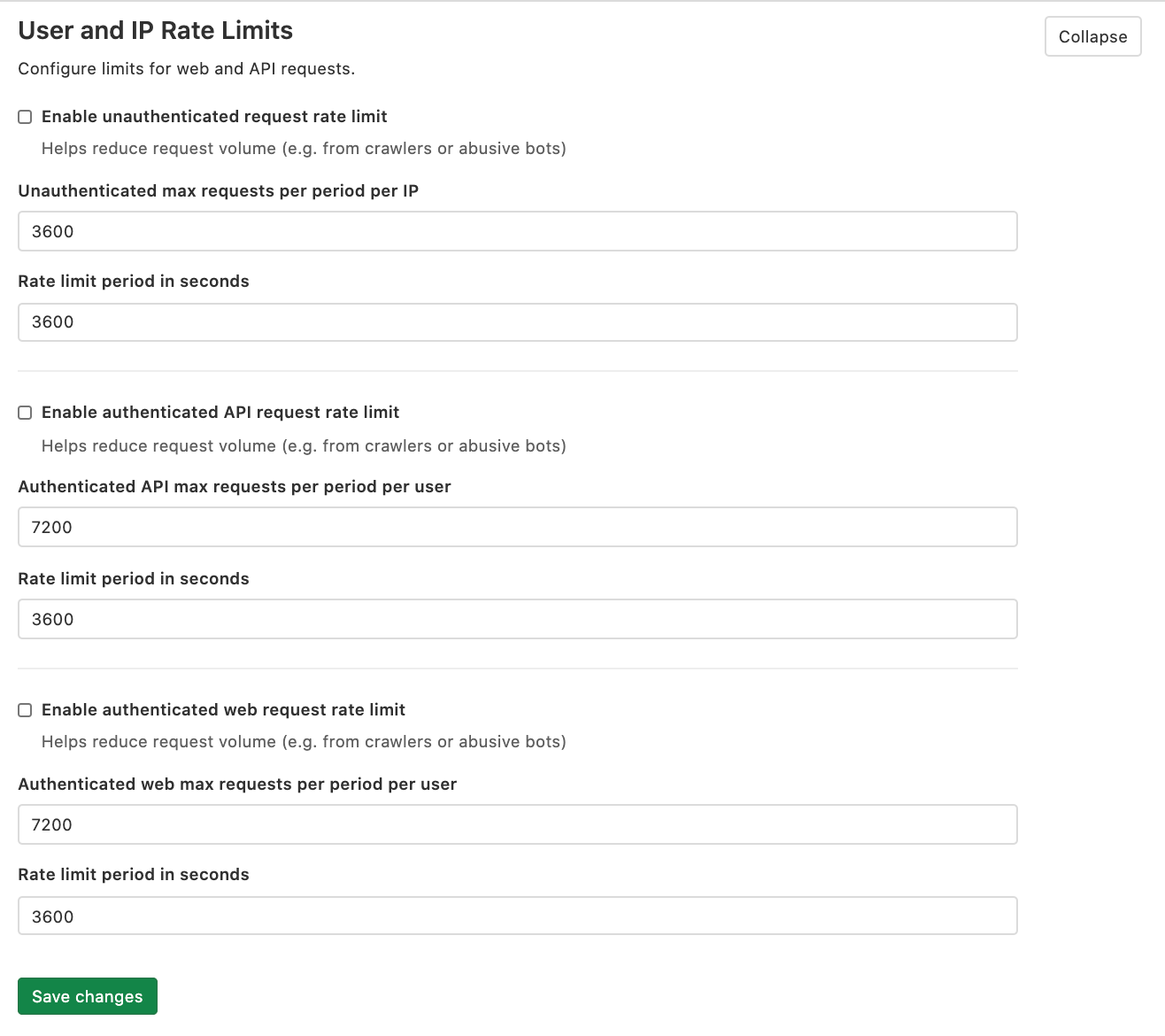
User and IP rate limits (CORE ONLY)
Rate limiting is a common technique used to improve the security and durability of a web application. For more details, see Rate limits.
The following limits can be enforced in Admin Area > Settings > Network > User and IP rate limits:
- Unauthenticated requests
- Authenticated API requests
- Authenticated web requests
These limits are disabled by default.
Use an HTTP header to bypass rate limiting
Introduced in GitLab 13.6.
Depending on the needs of your organization, you may want to enable rate limiting but have some requests bypass the rate limiter.
You can do this by marking requests that should bypass the rate limiter with a custom header. You must do this somewhere in a load balancer or reverse proxy in front of GitLab. For example:
- Pick a name for your bypass header. For example,
Gitlab-Bypass-Rate-Limiting. - Configure your load balancer to set
Gitlab-Bypass-Rate-Limiting: 1on requests that should bypass GitLab rate limiting. - Configure your load balancer to either:
- Erase
Gitlab-Bypass-Rate-Limiting. - Set
Gitlab-Bypass-Rate-Limitingto a value other than1on all requests that should be affected by rate limiting.
- Erase
- Set the environment variable
GITLAB_THROTTLE_BYPASS_HEADER.- For Omnibus,
set
'GITLAB_THROTTLE_BYPASS_HEADER' => 'Gitlab-Bypass-Rate-Limiting'ingitlab_rails['env']. - For source installations, set
export GITLAB_THROTTLE_BYPASS_HEADER=Gitlab-Bypass-Rate-Limitingin/etc/default/gitlab.
- For Omnibus,
set
It is important that your load balancer erases or overwrites the bypass header on all incoming traffic, because otherwise you must trust your users to not set that header and bypass the GitLab rate limiter.
Note that the bypass only works if the header is set to 1.
Requests that bypassed the rate limiter because of the bypass header
are marked with "throttle_safelist":"throttle_bypass_header" in
production_json.log.
To disable the bypass mechanism, make sure the environment variable
GITLAB_THROTTLE_BYPASS_HEADER is unset or empty.